Search
Items tagged with: infosec
I've personally grown to hate the security theatre of rotating my bank passwords every six months, especially because of requirements like "must contain one uppercase, one symbol, one lowercase, one special case and the blood of a unicorn."
When mathematically, a simple, grammatically incorrect sentence of 25 characters is much harder for a machine to crack than a gibberish 8-character password with symbols.
Entropy loves length.
I love the idea that the most secure key to your digital life could just be a weird little poem or an inside joke that only you know. Security doesn't have to be painful.
#infosec #passwords #cybersecurity #UX #security #sysadmin #programming #foss #linux #privacy #enshittification #reading #finance
PSA: @signalapp remains the most secure, privacy-preserving general purpose IM app safely and easily usable by non-techies.
👉 Don't let some randos on social media convince you otherwise.
If your very specific information security requirements meant you'd need to be using some other tool, you would have already known that, and would not be taking advice from social media posts. 👀
Vegetables are healthier than red meat.
Vaccines work and are safe.
Signal is secure.
Happy Data Protection Day!
20th anniversary online event: coe.int/web/data-protection/da…
#Data #DataProtection #DataPrivacy #Privacy #InfoSec #InformationSecurity #CyberSecurity #Encryption #E2EE #Security #PasswordManager #SelfHost #SelfHosted #SelfHosting #Linux #DataSovereignty #CouncilOfEurope #CoE #EDPS #EuropeanDataProtectionSupervisor #DPD #DPD2026 #OpenPGP #PGP #GnuPG #GPG #VeraCrypt #Tomb #LUKS #AES #P2P #VPN #LetsEncrypt #Argon2 #Tor #XMPP #OMEMO #TorBrowser #Tails #PrivacyBadger #JShelter
Apple security releases - Apple Support
This document lists security updates and Rapid Security Responses for Apple software.Apple Support
New advisory.
High severity NVIDIA runx vulnerability: CVE-2025-33234 nvidia.custhelp.com/app/answer… #Nvidia #vulnerability #infosec
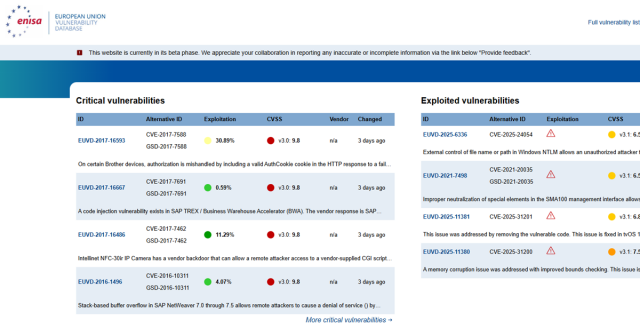
EUVD has listed critical CVE-2026-21962 Oracle HTTP Server vulnerability euvd.enisa.europa.eu/vulnerabi…
Oracle Critical Patch Update Advisory - January 2026 oracle.com/security-alerts/cpu… #infosec #vulnerability #Oracle
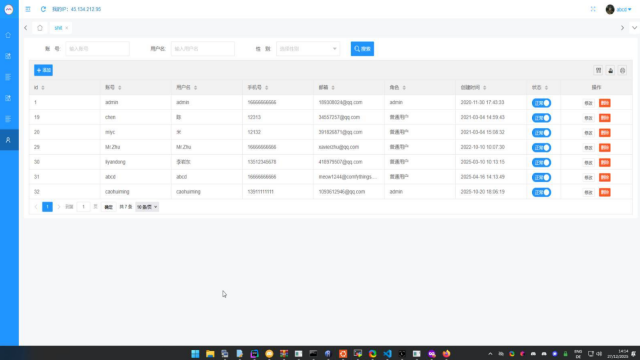
New, from me: Who Operates the Badbox 2.0 Botnet?
The cybercriminals in control of Kimwolf -- a disruptive botnet that has infected more than 2 million devices -- recently shared a screenshot indicating they'd compromised the control panel for Badbox 2.0, a vast China-based botnet powered by malicious software that comes pre-installed on many Android TV streaming boxes. Both the FBI and Google say they are hunting for the people behind Badbox 2.0, and thanks to bragging by the Kimwolf botmasters we may now have a much clearer idea about that.