Search
Items tagged with: StayFrosty
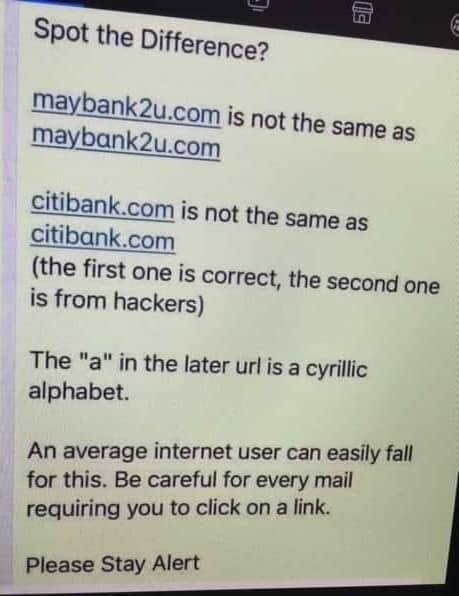
Hello friends, I've seen the below image come up a few times elsewhere and am going to expound a little!
While the hyperlinks in the image display correctly, those aren't actually the addresses of those sites! Instead, they're the Internationalized Domain Name replacements - examples of what are called IDN Homograph Attacks.
It's incredibly hard to include all characters from all active alphabets in the mechanisms that resolve domain names - so currently that letter set is restricted, and instead uses a translation system called Punycode to move between a visual URL with the correct characters and a domain name your computer can actually resolve to a website.
So while neurovagrant[.]com is fine either way, nӘ̃urovagrant[.]com isn't! The actually domain would be xn--nurovagrant-rkg322d[.]com.
Notice that xn-- ! That's what tells browsers and other software that it's an IDN domain, and to try and translate it.
Attackers use this to their benefit. So:
xn--mcrosoft-security-teams-1ec[.]com can appear in your email, on your twitter feed, in other places visually as: mícrosoft-security-teams[.]com
You may think you're signing in to check your retirement at vanguarɗ[.]com but it's actually sent you to xn--vanguar-4cd[.]com
A link that appears as vḙnmo[.]com actually sends you to the website xn--vnmo-q64a[.]com
They even target kids! Take a look at xn--rblox-jua[.]com - which looks like röblox[.]com in most settings. Note the diacritical mark above the first o.
If anything looks off, there's a reason. Always view links with skepticism, don't click on things unnecessarily, and always sign into the sites you use by going to the domain name you know.
Stay frosty out there, friends.